When Seconds Decide: Why Crypto AML Must Outpace Laundering Speed

In the first half of 2025, hackers stole more than $3 billion in cryptocurrencies. In some cases, funds began moving just seconds after the breach, with the entire laundering cycle completed before the incident even became public knowledge.
In this environment, traditional anti–money laundering (AML) mechanisms lose their effectiveness. The average time between the start of an attack and its disclosure exceeds 20 hours, giving criminals ample time to route assets through multiple platforms, obscure transaction trails, and off-ramp into fiat. As a result, even major platforms that fully comply with AML requirements risk becoming unwitting links in the laundering chain, and regulatory compliance alone is no longer a safeguard against reputational or legal fallout.
We will explore how crypto companies can analyze the speed and pathways of stolen asset movements, and, more importantly, how they can effectively protect their assets from malicious actors.
Based on Global Ledger’s Gone Fast: Laundering Timing Report (H1 2025).
Scale and New Realities of Crypto Hacks
In 2025, threats to the crypto industry are evolving not only in scale but also in sophistication. In the first six months of the year alone, 119 attacks were recorded — already one and a half times more than in all of 2024.
Centralized exchanges remain the top target for criminals, accounting for 54% of total losses, or about $1.6 billion. Next are smart contract vulnerabilities, which resulted in $517.8 million in losses. Compromised personal cryptocurrency wallets ranked third, with losses totaling $351.3 million.
At the same time, the nature of attacks is shifting from exploiting technical bugs to targeting systemic weaknesses:
- Malicious approval attacks, which accounted for only 7% of incidents, resulted in $1.46 billion in losses.
- Smart contract exploits made up 70% of incidents, yet resulted in a smaller $365.5 million loss.
- Private key compromises were involved in 16% of cases, causing $650.05 million in losses.
- Rug pull schemes were used in 6% of incidents, resulting in $514.07 million stolen.
This trend points to growing attacker interest in weaknesses in key management, user interfaces, and behavioral patterns. Market participants must reassess their priorities, as the prevalence of a threat does not always correlate with its potential financial impact.
Speed as the Decisive Factor
One of the defining features of cyberattacks in 2025 has been their speed. According to Global Ledger, in 68% of cases, funds were moved before the breach was made public. In 22.7% of incidents, the laundering process was fully completed before the disclosure of the attack.
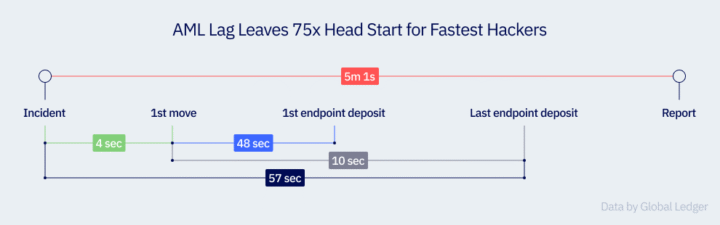
The absolute record was just 4 seconds from the moment of compromise to the first transaction. The shortest time from the first movement of funds to the first deposit at an endpoint address was 48 seconds. In the fastest cases, the entire laundering cycle took only 2 minutes and 57 seconds. Even average scenarios reveal a critical gap — the shortest time from incident to the first alert was 5 minutes and 1 second, which is 75 times slower than the reaction time of the fastest attackers.
On average, it takes 15.1 hours from the start of a breach to the first movement of funds. Public disclosure takes 37.2 hours, giving criminals more than a 20-hour head start. The average time to reach the first endpoint is 88 hours, and full movement of funds is completed within 195.5 hours. However, many attacks conclude before this point, and only 4.6% of stolen assets are ever recovered.
This timing advantage gives criminals a critical edge. In the hours before an official announcement, they can move assets through multiple platforms, split them into numerous transactions, and either cash out or shift them into ecosystems where tracking becomes significantly more difficult. Even with advanced monitoring and asset-freezing tools, a substantial portion of stolen funds is lost permanently under these conditions.
Channels for Moving Stolen Funds
The structure of stolen funds in 2025 has also shifted significantly. Cross-chain bridges have become the primary tool, accounting for more than half of all stolen assets in the first half of the year. Cryptocurrency mixers, previously the most popular laundering channels, were used to move around 11% of stolen funds. The appeal of bridges lies in their high throughput, rapid transaction speed, and relatively low level of regulatory oversight.
Centralized exchanges remain the main off-ramp for illicit funds. In 2025, about 15% of stolen assets were transferred to CEX accounts. Despite the growth of decentralized platforms, only 5.6% of stolen assets moved through DeFi solutions. Even when complying with AML requirements, exchanges often face the problem that by the time suspicious funds are detected, they have already passed through multiple transactions involving stolen assets.
A notable example was the Bybit hack, in which $1.38 billion of the $1.456 billion stolen was routed through cross-chain bridges. This case clearly shows that attackers favor tools that allow them to move large sums between networks quickly and in a few large transactions.
Global Ledger analysts also note that in 2025, not all stolen assets were spent immediately. More than half of the stolen funds remained unmoved, nearly 13% were frozen or burned, and only 4.6% were recovered.
Why Existing AML Procedures Fall Short
Even when platforms use modern monitoring tools, their effectiveness is diminished by delays in incident handling. The average response window — the time available once stolen funds have already reached the platform — is only 10 to 15 minutes. If no action is taken within this timeframe, the assets are typically moved to mixers, other exchanges, or cashed out. Once that happens, recovery becomes nearly impossible.
Most operators still rely on manual reviews of suspicious transactions. This model is not designed for instant response and often results in delays. Additional time is lost verifying requests, confirming the authority of the requester, and coordinating the next steps.
Key factors slowing down AML processes include:
- Manual reviews instead of real-time automated analysis.
- Delays in information exchange between platforms and law enforcement.
- Legal constraints — for example, companies can freeze funds for up to seven days, while police may require more than 30 days to initiate seizure.
- Challenges in cross-border cooperation and the lack of unified standards for defining the legal status of digital assets.
As a result, many incidents that could have been prevented or mitigated remain unaddressed. At the current pace of breach disclosure, AML teams often learn about an attack only after the funds have been irretrievably lost.
What Will Help AML Teams Act Faster
Reducing response time to cyberattacks requires simultaneous changes in technology, organizational processes, and industry-wide collaboration. In a world where stolen funds can be laundered in minutes, the priority must be instant detection and blocking of suspicious transactions.
Key measures include:
- Automated real-time analysis powered by artificial intelligence (AI). Such systems should compare transactions against thousands of known fraud patterns, detect anomalies and novel attack types, and continuously self-learn from new incident data.
- Platform-native intelligence. This includes user behavior analysis, device fingerprinting, login attempt monitoring, and internal risk markers. Such capabilities enable the detection of threats that cannot be identified by external services.
- Front-end transaction blocking. Integrating risk signals from analytics and infrastructure partners directly into the user interface to prevent the initiation of a transaction if the wallet is flagged as suspicious.
- Coordination with infrastructure providers and token issuers. Stablecoins with built-in freeze functionality, such as USDC and USDT, allow transactions to be stopped within seconds when a threat is confirmed.
- Direct channels to law enforcement. Standardized freeze request formats (case ID, wallet addresses, TxID, AML flags), designated contact persons, and pre-signed cooperation agreements significantly reduce reaction time.
- Escalation procedures. A clear, documented process for responding to incidents — including automatic blocking and immediate notification of responsible personnel — lowers the risk of reputational and licensing consequences.
“To truly stay ahead, we need AI-powered real-time detection, able to evaluate a live transaction against thousands of known fraud templates and dynamically identify anomalies or novel attack types, as well as continuous self-learning algorithms, which evolve based on emerging fraud patterns,” notes Max Krupyshev, CEO of CoinsPaid.
When criminals operate with a head start measured in hours and speeds measured in seconds, formal regulatory compliance is no longer sufficient protection. For regulators, unintentional involvement in the laundering chain is no excuse and can lead to sanctions, license revocation, and reputational damage.
“If we continue to react the way we do today, AML will remain a post-incident reporting tool rather than an asset protection mechanism. Reaction time must be measured in seconds, otherwise, we lose by definition,” states the Global Ledger report.
The future of AML in the cryptocurrency industry will depend directly on the ability to act faster than the attackers. This will require process automation, advanced behavioral analytics, and close cooperation between platforms, infrastructure providers, and law enforcement agencies. Those who can build such a model will gain not only a competitive advantage but also the trust of their customers.











