Many members of the crypto community mistakenly believe that any user can extract and analyze data from the blockchain. There’s some truth to this, as public blockchain networks are highly transparent environments. However, each blockchain is a huge, isolated database per se. That’s why targeted analysis of specific data sets and their interrelationships requires special tools and, more importantly, specially trained professionals.
When it comes to investigating hacks of Web3 projects and other crypto incidents, on-chain analysis skills aren’t enough. You also need skills in interacting with law enforcement and legal support. Andrei Kutin, CEO of Match Systems, spoke about all this using specific cases as an example.

Finding and Recovering Stolen Crypto-Assets
Is it possible to track down and recover stolen cryptocurrencies? Yes, it is.
Investigations conducted by Match Systems specialists comply with the requirements of criminal procedures and can be used in courts as evidence of unlawful acts and respective material damage.
According to the research results, Match Systems experts can determine the ways of movement of crypto-assets in the vast majority of cases. If the endpoint of funds movement is a centralized exchange, AML/CFT specialists provide assistance in drafting a request and sending it to the exchange in order to block and recover crypto-assets.
Recovery of $100K Worth of Stolen Digital Assets
Example: over $100,000 worth of crypto-assets were stolen from the victim through social engineering techniques.
Investigation results: on-chain analysis revealed that all stolen assets were transferred to the centralized exchanges Binance and Gate.
Outcome: the investigation materials were sent to law enforcement agencies, and a criminal case was initiated. By court order, the funds on centralized crypto exchanges were frozen, after which they were returned to the victim.
Blocking of $500K Scam Project Organizers Stole as Investment
Example: the victim was tricked into investing $500,000 in a scam project.
Investigation results: on-chain analysis revealed that cryptocurrency assets were transferred to non-custodial (cold) wallets and remain there. To date, the available crypto addresses have been placed on the monitoring system. In case of the movement of assets and their transfer to centralized exchanges, the necessary measures will be taken timely.
Outcome: crypto wallets with illegally obtained funds are monitored. Any attempts of attackers to withdraw assets will most likely end with their return.

Obtaining Relevant Information on Methods of Laundering Proceeds from Crime
Is it possible to deanonymize a criminal organization engaged in crypto crimes? Yes, it is.
Match Systems specialists develop and implement anti-money laundering policies and identify clients of crypto services in accordance with the current requirements of regulators. When conducting investigations, specialists also use open source intelligence (OSINT) methods in their work for the most complete and comprehensive reflection of information.
As part of regular monitoring, new ways and methods of laundering criminal proceeds are identified and databases on them are updated.
Stopping Money Laundering Via Telegram Bot
Example: information was received about a Telegram bot that was used for money laundering.
Investigation results: on-chain analysis revealed that crypto-assets coming to wallets controlled by the Telegram bot’s administrators were sent to decentralized services for money laundering, then transferred to centralized exchanges, and paid out to users of the services. The study used software tools for analyzing decentralized exchange services developed by Match Systems. Using OSINT methods, identities of the Telegram bot’s administrators were discovered.
Outcome: the Telegram bot submitted for research was fully deanonymized, and the data was handed over to representatives of law enforcement agencies.

Identification of Persons Involved in Commission of Certain Transactions
Is it possible to find a criminal involved in crypto offenses? Yes, it is.
Due to the fact that the blockchain network stores information about all transactions performed, identifying each transaction with a separate hash identifier, Match Systems AML/CFT specialists can track all movements of certain crypto-assets and establish connections with specific exchanges or exchange services. In turn, this helps identify the details of real individuals carrying out tracked transactions.
Identifying Drug Dealer
Example: according to the information received, the user who made the transfer with a certain hash identifier is involved in drug trafficking.
Investigation results: on-chain analysis traced the chain of transactions to a centralized exchange, which helped identify the person who made the transfer with the hash identifier under study.
Outcome: the identity of the alleged criminal was established, and the research materials were transferred to law enforcement agencies.

Study and Analysis of Specific Website
Is it possible to check the reliability of a counterparty in the Web3 environment? Yes, it is.
Large crypto projects (exchanges, exchangers, etc.) use not just one cryptocurrency address in their activities, but a crypto wallet (cluster) that contains many addresses. The clustering principle is based on making a single spend on several crypto addresses in one transaction or receiving change to one of the addresses when making the transaction with another address in this cluster.
The correct segmentation of clusters makes it possible to identify all addresses belonging to one manager and significantly expand the possibilities of further analysis, including working out the connections of each of these addresses and establishing their involvement in illegal activities.
Analyzing Cryptocurrency Exchanger
Example: the client provided a crypto exchanger for analysis, with which it was planned to conduct business activities.
Investigation results: on-chain analysis revealed that the exchanger often directly interacts with addresses categorized as fraud, darkmarket, stolen funds, etc. in its activities. Thus, it can be concluded that the investigated exchanger doesn’t comply with AML/CFT requirements, which creates favorable conditions for laundering criminal proceeds.
Outcome: the client was recommended to introduce a crypto compliance system to prevent transactions with high-risk assets.

P.S. Don’t waste your time and trust professionals!
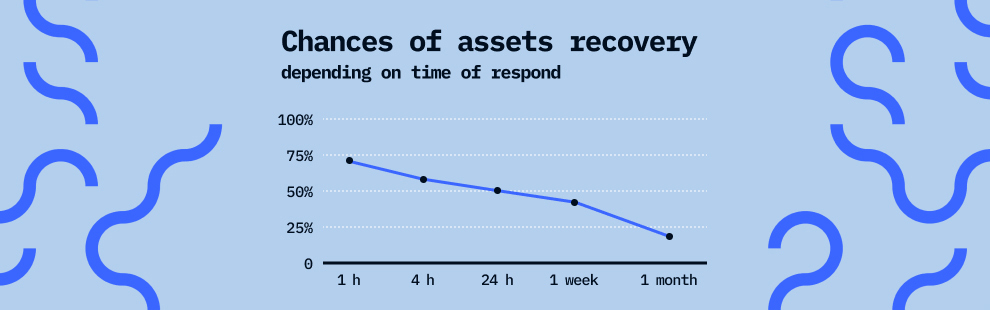
Keep in mind that if your cryptocurrency has been stolen, time matters! The sooner you contact specialists to find and return stolen cryptocurrencies, the more chances you have to recover your funds and catch the attacker! The image below shows the correlation between the elapsed time and the chances of recovering stolen funds.
Match Systems currently provides comprehensive support for all activities related to blockchain and crypto-asset analytics. The Match Systems team has full technical and human resources assistance to conduct the most complete and highest quality analysis of blockchain activities.